It appears that Locky (so called due to the file extension *.locky that the encrypted files take on) is predominantly distributed via email within infected Microsoft Office attachments such as Word or Excel documents delivered through phishing campaigns.
Victims are hit with a message advising they have been hit with instructions on how to pay.
See example below:
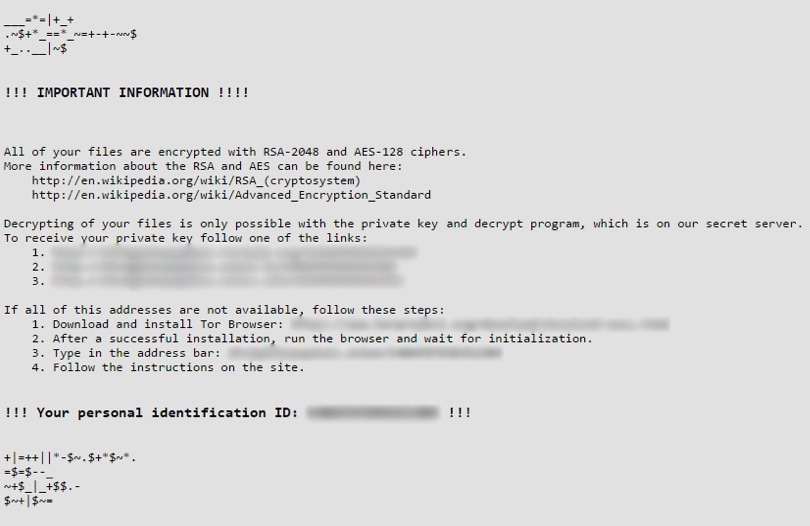
How does Locky work?
According to Palo Alto Networks, these malicious emails use the following convention for the email subject text:
ATTN: Invoice_J-< 8-digits>
With the following matching figures used for the subject text and attachment name:
Subject: ATTN: Invoice J-11256978
Attachment: invoice_J-11256978.doc
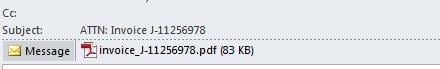
These attachments are documents that contain macros which, if allowed to run, download a Bartallex installer which installs the Locky ransomware on the victim machine.
According to McAfee, the following registry keys are indicators of infection:
HKEY_CURRENT_USER\ Software\Microsoft\Windows\CurrentVersion\Run:
“Locky" = “%TEMP%\<random name>.exe”
HKEY_CURRENT_USER\Software\Locky:
- "id" = < Personal Identification ID>
- “pubkey” = < RSA public key received from the CnC Server >
- “paytext” = < Content of “Locky_recover_instructions.txt” >
- “completed” = “0x1” [This value will be added after completion of encryption]
On execution, Locky usually copies itself into the %temp% folder with a randomly named “.exe” file:
E.g.: C:\Users\<UserProfile>\AppData\Local\Temp\<random name>.exe
In order for the ransomware to begin encrypting victim files, it must first communicate with a Command and Control (C&C) server. It encrypts its own communications using a specific algorithm and keys. Once it receives the public RSA key for the C&C server, it reports back a range of information to the server, including:
- Encryption statistics
- Path of affected files
- List of encrypted files
- Language of affected machine
Communication with C&C servers is carried out over a wide range of IPs and URLs.
Infection file targeting
Locky is designed to target all accessible files on the victim’s local machine, as well as files on any attached removable and network drives. Additionally, cloud based storage such as Google Drive and Dropbox could have files encrypted and synced which may affect multiple other users’ access to those files within shared accounts.

Files are encrypted using RSA-2048 and AES-1024 algorithms and the resultant file contains a .locky extension, then displaying the message (as above) explaining how to pay to get the files decrypted.
Organizations are then faced with the much talked about dilemma: “Do we pay?”
Our advice is not to pay, but to prepare.






