Creating Good PCI-DSS Network and Data Flow Diagrams
Written by: Leo Boike
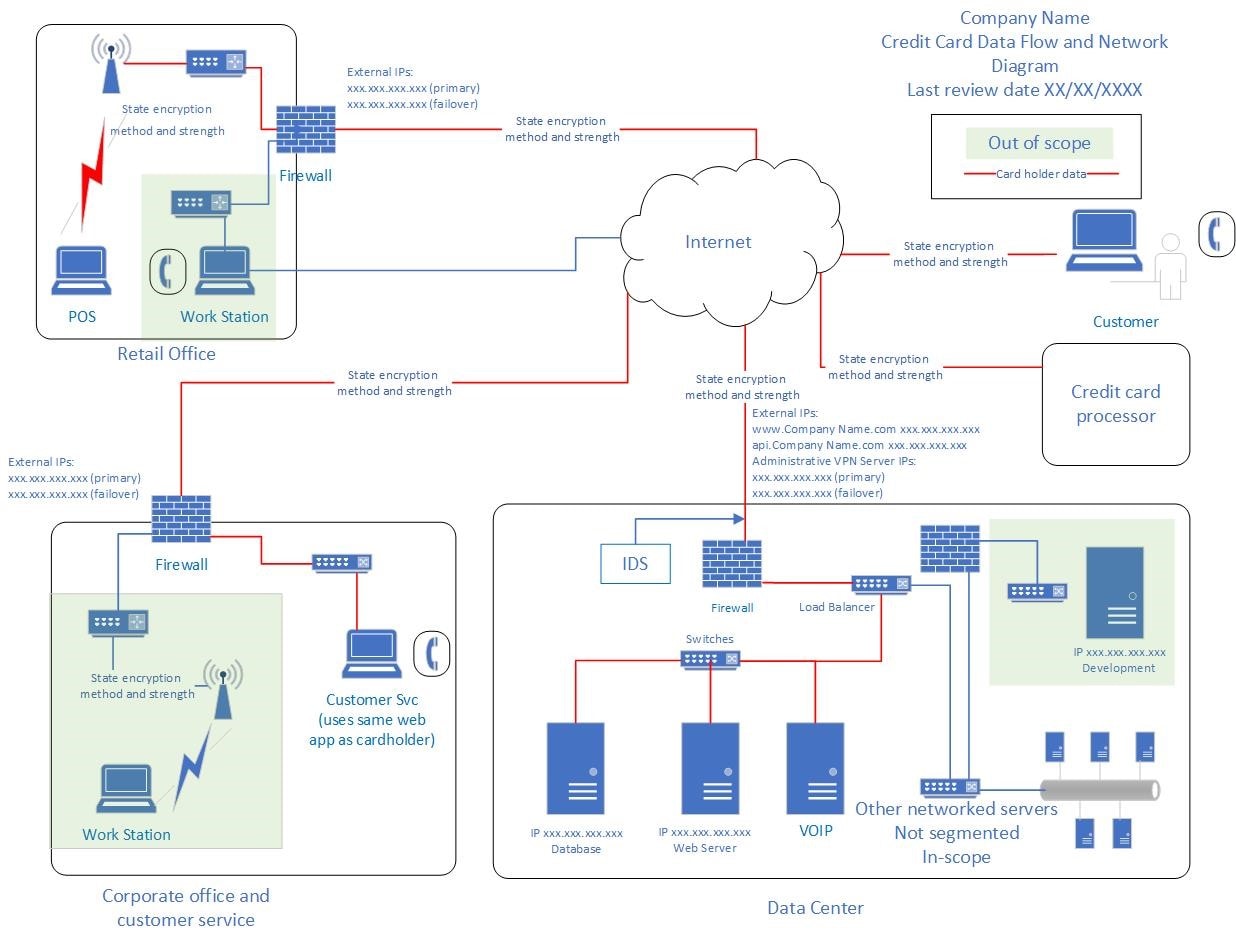
The most useful documents required of PCI-DSS are covered in PCI-DSS requirements 1.1.2 (network diagram) and 1.1.3 (data flow diagram). Depending on the complexity of your network and processes, you could have one combined network and data flow diagram or you may require multiple diagrams.
Let’s first break down requirements 1.1.2 and 1.1.3 and then take a look at steps to make a good diagram.
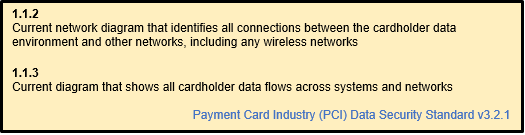
The keywords in these requirements are:
Current – In planning a road trip across country by car, I would not want to use a map that was not updated since 1955. Roads have changed and new freeways would have been added that would not be on the 1955 map.
In the same fashion, in planning changes to my environment or in planning and validating security solutions and controls, I need to have the most up to date and accurate depiction of my network.
The best way to stay current is to add a step to your change control process and ask after every change:
- Do I need to update the network diagram?
- Do I need to update the data flow diagram?
Review your diagrams at least every six months and after any major changes to your systems.
Network – This means your entire network. The diagram shows not only where you store, process or transmit cardholder data, but also how you have segmented those networks and system components that do not store, process or transmit cardholder data. The requirements specifically mention wireless networks. Inadequately configured or maintained wireless access points are a security risk. All wireless networks need to be included in the network diagram to show how they are connected to or isolated from the cardholder data environment.
Larger organizations with complex networks or companies that have more than one acceptance channel might consider creating multiple diagrams.
For a good network diagram, you need to know what devices you have, and where are they located. The first place to start is to maintain an inventory of all your devices, physical locations, and their function. This includes routers, servers, switches, firewalls, VPN concentrators, SSH modems, etcetera. This list must also include virtual devices.
All connections and All cardholder data flows – means just that, ALL CONNECTIONS and ALL CARDHOLDER DATA FLOWS. Many companies have been breached because they did not account for, and thus did not have appropriate security controls on, components that are connected to their network. This includes systems and processes that may have nothing directly to do with cardholder data, such as environmental control systems, or third-party solutions that are used to support your cardholder data environment.
To get a comprehensive picture of your network connections and cardholder data flows, you need to:
- Maintain an inventory of all your devices, physical locations, and their function
- Maintain an inventory of all applications in use, including applications used to maintain and monitor your systems
- Maintain a list of vendors that you share cardholder data with or who can affect the security of your cardholder data. The list must also include what role the vendor plays in your cardholder data environment
- Understand from an operational perspective how cardholder data enters your network, travels through your network, is stored in your network, exits your network, and to where and whom that cardholder data is being shared. Talk with and review processes with business teams, finance, and accounting. Review operational procedures and speak with the users and application development teams and not just networking and technical staff. Talking with operational staff on how they “do things” will uncover systems and applications you may not have thought about. A few questions to ask are:
- How is the data received (phone, mail, email)?
- How is it entered (automated, manually keyed)?
- Is the application in-house or located at third party?
- How and what data is being transmitted?
Using the above information:
- Map out the physical locations of devices (Corporate headquarters, data centers, third-party vendors and third-party hosting sites, etc.)
- Show how the devices are connected
- Show any VLANs or other segmentation
- Show connections between the cardholder data entry points and exit points to show how the data travels through your network
- Fill in details such as IP addresses, ports and protocols in use, encryption methods and algorithms in use, etc.
- Indicate where cardholder data is transmitted and stored
- Include wireless devices/networks
- Indicate the date when it was last updated and reviewed
A detailed network diagram and a detailed cardholder dataflow diagram is indispensable for:
- Determining how proposed changes may affect your network and security standing
- Helping you better plan out projects, including any necessary remediation that may be required to meet PCI-DSS
- Helping with risk assessments by providing a clear picture of your environment
- Helping with presentations to auditors and other parties that require a network overview
- Meeting requirements for PCI-DSS
Below is an example of a simple combination network and card holder data flow diagram.