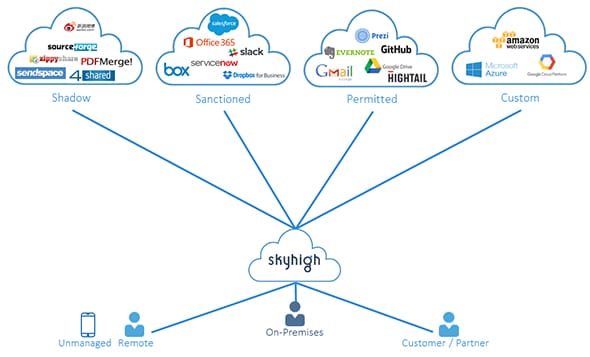
One platform for all cloud services
BSI partner with McAfee to provide a Cloud Access Security Broker (CASB) solution to our clients. We partner with market leading providers to complement our offering. McAfee MVISION Cloud (Skyhigh Networks) is a Gartner and Forrester solution trusted by enterprises to protect their data in thousands of cloud services.With this solution, organizations can leverage a single cross-cloud platform to gain visibility into cloud usage and risks, meet compliance requirements, enforce security policies, and detect and respond to potential threats.