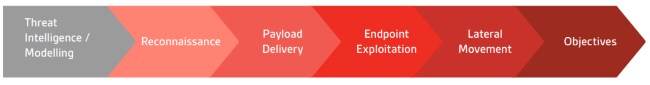
Attack Simulation webinar series
How well prepared are you and your organization to prevent, detect, respond and recover from an attack? To learn how attack simulation services and red teaming techniques can help build your organization's security posture, watch our three-part webinar series including a unique real-world demonstration.